Privileged Access
Management (PAM)
Introduction
Privilege access management is part of IAM, helping manage entitlements, not only of individual users but also shared accounts such as super users, administrative or service accounts. A PAM tool, unlike IAM tools or password managers, protects and manages all types of privileged accounts. Mature PAM solutions go even further than simple password generation and access control to individual systems, and also provide a unified, robust, and—importantly—transparent platform integrated into an organization’s overall identity and access management (IAM) strategy.
How PAM helps organizations?
PAM helps organizations condense their organization’s attack surface, and prevent, or at least mitigate, the damage arising from external attacks as well as from insider malfeasance or negligence.
The only method of preventing threats is by effectively managing and tracking privileged user sessions. Through streamlining the authorization and control of privileged accounts, PAM lets organizations stay in control and be safe from both intentional and unintentional admin rights abuse.
Request more information about PAM solutions
Difference between the two major categories of IT accounts
There are two major categories of IT accounts:
USER ACCOUNTS
A user account typically represents a human identity (such as an Active Directory user account) and has an associated password to Protect information and prevent anyone else accessing without permission. There is usually a single account password per user that needs to be memorized by a person.
PRIVILEGED ACCOUNTS
Privileged accounts provide administrative or specialized levels of access to enterprise systems and sensitive data, based on higher levels of permissions. A privileged account can be associated with a human being or non-human IT system.
Organizations often have two to three times more privileged accounts than they have employees. In most organizations, IT staff have one account with standard-level permissions and another account for performing operations that require elevated permissions.
What are the risks associated
with unmanaged privileged accounts?
Many recent high-profile breaches have one thing in common: They were accomplished through the compromise of privileged credentials. Industry analysts estimate that up to 80% of all security breaches involve the compromise of privileged accounts.
Virtually all organizations have some unknown or unmanaged privileged accounts, increasing their risk. Some may have thousands. This can happen for various reasons:
-
-
-
- An ex-employee’s access was never disabled.
- An account is utilized less and less often until it becomes obsolete and is abandoned.
- Default accounts for new devices were never disabled.
-
-
Every unknown or unmanaged privileged account increases your organization’s vulnerability and presents an opportunity for an intrusion. An employee may access it to perform unauthorized tasks, intentionally or unintentionally, breaking compliance regulations and increasing your liability. A disgruntled ex-employee who retains privileged access cause harm.
A cyber-criminal can find the account and penetrate your organization, steal information, and wreak untold havoc.
If a single privileged account is used across your organization to run many services or applications, when that account is breached, your risk increases exponentially. In that case, it only takes one compromised privileged account for an attacker to gain access to virtually any information within your organization’s IT network.
How do cyber-criminals
compromise privileged accounts?
1. Compromise a local account.
2. Capture a privileged account.
3. Hide and observe.
4. Impersonate employees.
5. Establish ongoing access.
6. Cause harm.
Why is PAM important?
Strong perimeter protections installed to stop malicious attacks are rendered powerless if a bad actor has already bypassed firewall defenses using an active user account. Compromised accounts are a very common vulnerability and a particularly difficult challenge for network managers. In fact, Verizon’s 2017 Data Breach report cited 81% of hacking-related breaches leveraged either stolen and/or weak passwords. This type of system breach is hard to detect unless strict controls and comprehensive activity monitoring is in place. For PAM tools, this is the primary function.
Privileged accounts, also known as administrative accounts, have access to critical data and infrastructure. Certain users play a vital role in ensuring network efficiency, however, the embedded permissions of their privileged accounts make them high-value targets for bad actors.
A well-executed privileged access management strategy establishes regulated individual user access controls and behaviour transparency to mitigate security risks. PAM tools are introduced to ensure that users only have access to what is required to do their job and nothing more.
Why would I need PAM?
PAM keeps your organization safe from accidental or deliberate misuse of privileged access.
Some of these admin users can override existing security protocols.
PAM solves this problem.
A PAM solution offers a secure, streamlined way to authorize and monitor all privileged users for all relevant systems.
- Grant privileges to users only for systems on which they are authorized.
- Grant access only when it’s needed and revoke access when the need expires.
- Avoid the need for privileged users to have or need local/direct system passwords.
- Centrally and quickly manage access over a disparate set of heterogeneous systems.v
- Create an unalterable audit trail for any privileged operation.
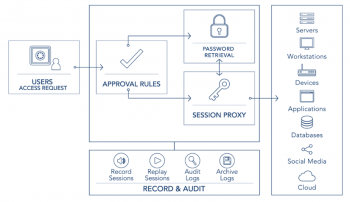
Capabilities of the PAM solution
Components of a PAM Solution
Privileged Access Management solutions vary in their architectures, but most offer the following components working in concert: