A denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
In a distributed denial-of-service attack (DDoS attack), the attack traffic flooding the victim originates from many different sources. This effectively makes it impossible to stop the attack simply by blocking a single source.
Challenges
DoS attacks target sites or services hosted on high-profile web servers such as banks or credit card payment gateways.
In 2018, the largest DDoS attack in history, reaching a peak of about 1.7 terabits was directed to an unnamed customer of service provider Arbor Networks. A few days earlier, GitHub was hit by an attack of 1.35 terabits per second.
Some common examples of DDoS attacks are UDP flooding, SYN flooding and DNS amplification. An application layer DDoS attack (sometimes referred to as layer 7 DDoS attack) is a form of DDoS attack where attackers target application-layer processes. The attack over-exercises specific functions or features of a website with the intention to disable those functions or features. This application-layer attack is different from an entire network attack and is often used against financial institutions to distract IT and security personnel from security breaches. An advanced persistent DoS (APDoS) attack requires specialised DDoS mitigation. The longest continuous period noted so far lasted 38 days. This attack involved approximately 50+ petabits (50,000+ terabits) of malicious traffic. Degradation-of-service attacks, where short-lived floodings of victim websites will cause slowing it rather than crashing it, can be more difficult to detect and can disrupt and hamper connection to websites for prolonged periods of time, potentially causing more overall disruption than a denial-of-service attack. Permanent denial-of-service (PDoS), an attack that damages a system so badly that it requires replacement or reinstallation of hardware. Amplification attacks are used to magnify the bandwidth that is sent to a victim. This is typically done through publicly accessible DNS servers that are used to cause congestion on the target system using DNS response traffic. Many services can be exploited to act as reflectors, some harder to block than others.
These are just a few examples, the threat requiring the adoption of countermeasures.
Countermeasures
Protect organization domain names by using registrar locking and confirming domain registration details (e.g. contact details) are correct.
Ensure 24x7 contact details are maintained for service providers and that service providers maintain 24x7 contact details for their customers.
Implement availability monitoring with real-time alerting to detect denial-of-service attacks and measure their impact.
Partition critical online services (e.g. email services) from other online services that are more likely to be targeted (e.g. web hosting services).
Pre-prepare a static version of a website that requires minimal processing and bandwidth in order to facilitate continuity of service when under denial-of-service attacks.
Use cloud-based hosting from a major cloud service provider (preferably from multiple major cloud service providers to obtain redundancy) with high bandwidth and content delivery networks that cache non-dynamic websites.
How can this technology help you?
DDoS attacks cause major disruptions in the business processes leading to major losses both in public image and financial. Firewalls and other traditional defences are only effective in part or not at all.
All the above countermeasures are common-sense, but require some action where time to response is critical. They do not replace deploying an Anti-DDoS system, either on-premises, in the Cloud, or better both, to mitigate the effects of the attack as it happens.
Advantages
By using the appropiate anti-DDos technologies, companies may conduct their day-to-day businesses as usual, with no or limited inconveniences. Clients will access the under-attack systems and these will respond in a timely manner. Due to the amount of traffic involved in a DDoS attack, it makes sense to combine on-premise defences with scrubbing center services. This way traffic exceeding the perimeter capacity is passed through the scrubbing center and only clean traffic will reach the premises. Scrubbing center subscriptions are based on both clean traffic and/ or total attack capacity, the former being an advantage for businesses that are sensible to their services availability.
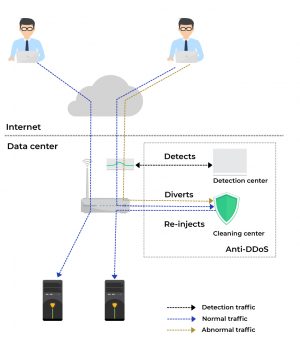
Deployment options
Deployment options include on-premise, cloud and a hybrid of the two. The latter employs an on-premise device that detects and mitigates the attack up to a point fater which the cloud solution (scrubbing center) takes over.
Mitigation
Defensive responses to denial-of-service attacks typically involve the use of a combination of attack detection, traffic classification and response tools, aiming to block traffic that they identify as illegitimate and allow traffic that they identify as legitimate. Several techniques are part of the response to such attacks, some of them being Bandwidth Management, Application level Key Completion Indicators, Blackholing and Sinkholing, IPS, DDS (DoS Defense Systems), Upstream filtering (Scrubbing Centers).