Threat Intelligence
Threat Intelligence
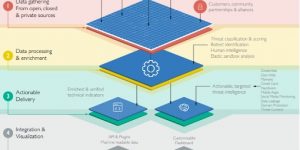
What is Threat Intelligence technology?
Threat intelligence is knowledge that allows you to prevent or mitigate cyberattacks. Rooted in data, threat intelligence gives you context that helps you make informed decisions about your security by answering questions like who is attacking you, what their motivations and capabilities are, and what indicators of compromise in your systems to look for.
Challenges
Today, the cybersecurity industry faces numerous challenges — increasingly persistent and devious threat actors, a daily flood of data full of extraneous information and false alarms across multiple, unconnected security systems, and a serious shortage of skilled professionals.
How can Threat Intelligence technology help?
Automatically identifying and dismissing false positives
Enriching alerts with real-time context, like custom risk scores
Comparing information from internal and external sources
Detect actions that are more likely to be innocuous rather than malicious
Identify attacks that are not relevant to that enterprise
Payment fraud
Monitoring sources like criminal communities, paste sites, and other forums for relevant payment card numbers, bank identifier numbers, or specific references to financial institutions can provide early warning of upcoming attacks that might affect your organization.
Compromised data
Cybercriminals regularly upload massive caches of usernames and passwords to paste sites and the dark web, or make them available for sale on underground marketplaces. Monitor these sources with threat intelligence to watch out for leaked credentials, corporate data, or proprietary code.